Storage Area Network
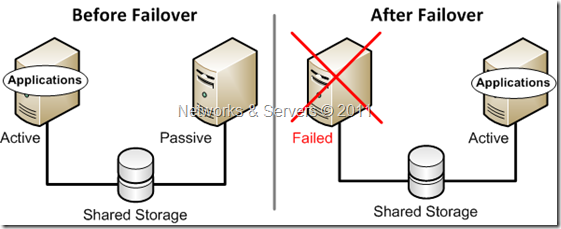
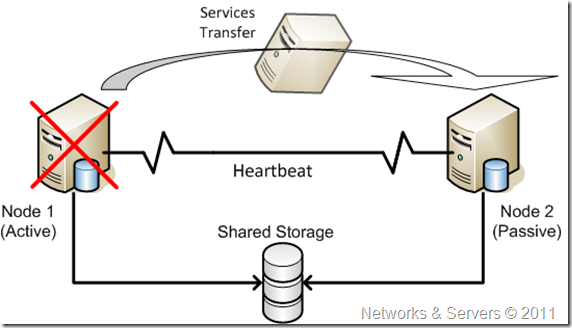
A Storage Area Network (SAN) is a dedicated high-performance subnet that provides access to consolidated, block level data storage and is primarily used to transfer data between computer systems and storage elements and among multiple storage elements, making storage devices, such as disk arrays, tape libraries, and optical jukeboxes, accessible to servers so that the devices appear like locally attached devices to the operating system.

A SAN typically has its own communication infrastructure that is generally not accessible through the local area network by other devices. A SAN moves data among various storage devices, allowing for the sharing data between different servers, and provides a fast connection medium for backing up, restoring, archiving, and retrieving data. SAN devices are usually installed closely in a single room, but they can also be connected over long distances, making it very useful to large companies.
SAN Benefits
The primary benefits of a SAN are:
- High Availability: One copy of every piece of data is always accessible to any and all hosts via multiple paths;
- Reliability: Dependable data transportation ensures a low error rate, and fault tolerance capabilities;
- Scalability: Servers and storage devices may be added independently of one another and from any proprietary systems;
- Performance: Fibre Channel (the standard method for SAN interconnectivity) has now over than 2000MB/sec bandwidth and low overhead, and it separates storage and network I/O;